
[ad_1]
A new Report Cybersecurity firm Netskope has disclosed details of a campaign that abused Microsoft Sway and CloudFlare Turnstile and used QR codes to trick users into providing Microsoft Office credentials to phishing platforms.
The campaigns targeted victims in Asia and North America and spanned a variety of sectors including technology, manufacturing and finance.
What is quisching?
QR Code It is a convenient way to browse websites or get information without typing any URL on your smartphone. But using QR codes has risks: cybercriminals can abuse QR codes to lead victims to malicious content.
This process is called “baiting,” where victims are redirected to malicious websites or prompted to download harmful content by scanning a QR code. Once on the website, cybercriminals steal your personal and financial information. QR codes are designed so that users have no idea where the code will lead them after scanning it.
Thomas Damonneville, head of anti-phishing company Tracking PhishingQuiishing “is a growing trend,” he told TechRepublic, “it’s very easy to use and makes it harder to check if the content is legal.”
Quishing attack via Microsoft Sway
In July 2024, Netskope Threat Labs saw a 2,000-fold increase in traffic to phishing pages via Microsoft Sway. Most of the malicious pages used QR codes.
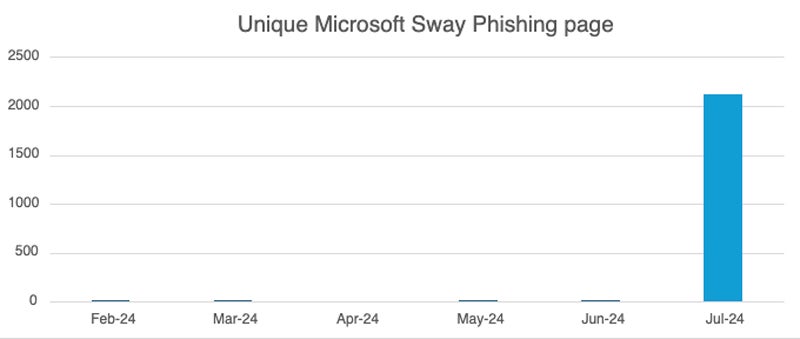
Microsoft Sway is a free online application from Microsoft Office that allows users to easily create presentations or other web-based content. The fact that it is free makes it an attractive target for cybercriminals.
In the campaign revealed by Netskope researcher Jan Michael Alcantara, victims were targeted with Microsoft Sway pages that led attackers to attempt to harvest Microsoft Office credentials.
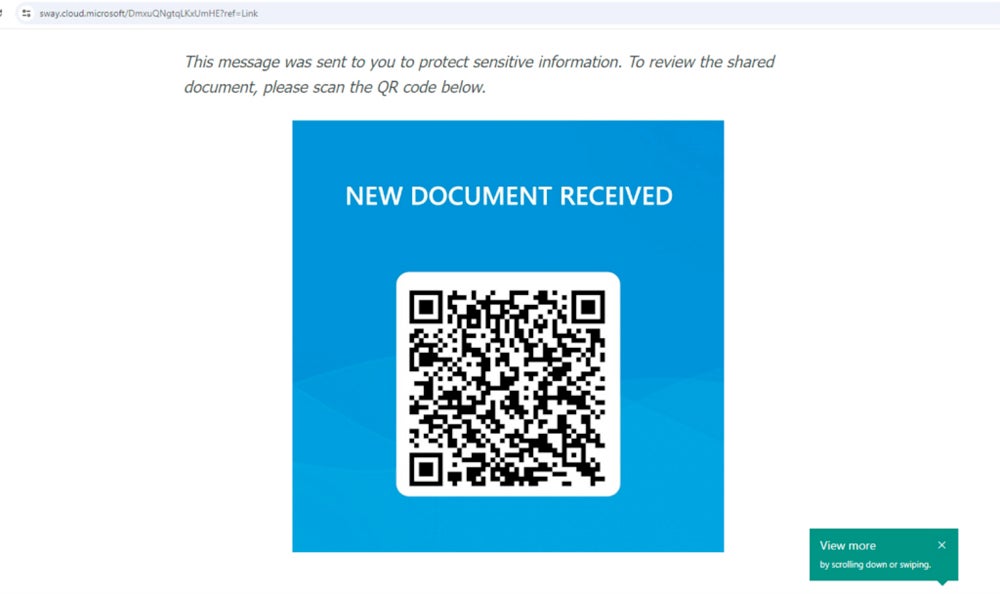
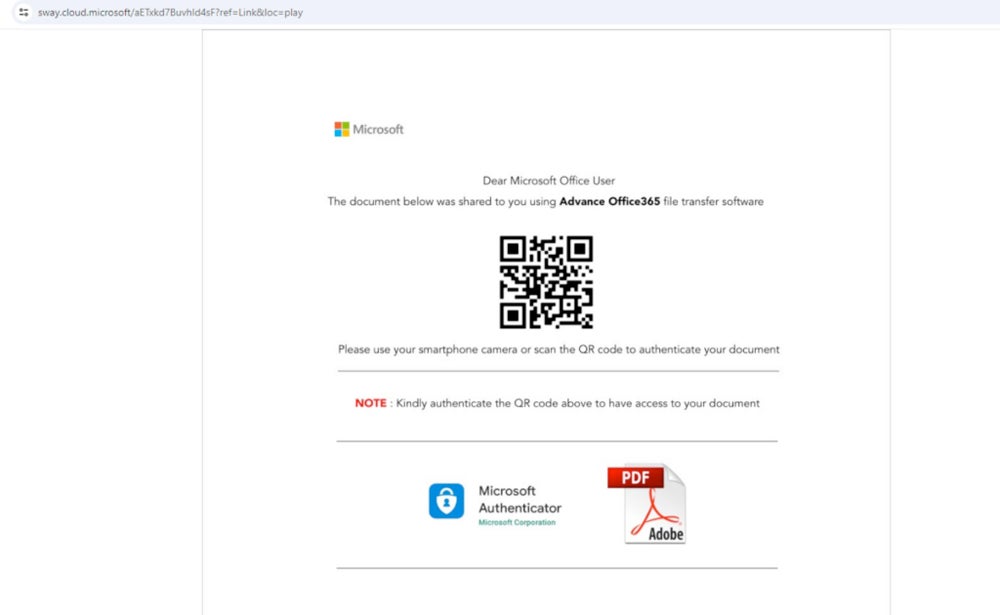
Netskope’s research did not mention how the fraudulent links were sent to victims, but it is possible that they were spread via email, social networks, text messages or instant messaging apps.
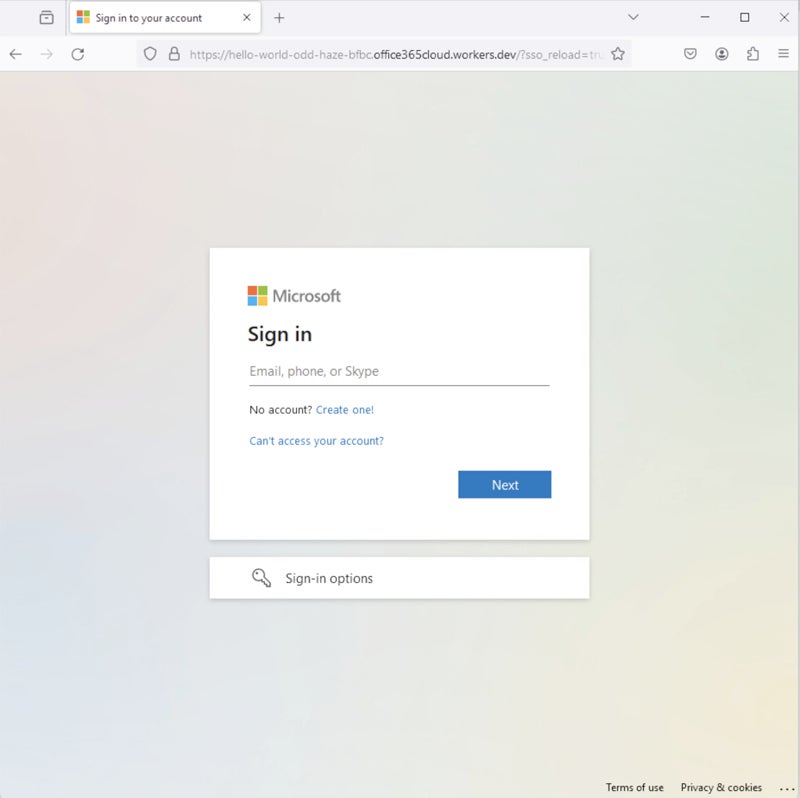
The final payload looks similar to a legitimate Microsoft Office login page, as revealed in May 2024. release From the same researchers.
Stealthy attacks using CloudFlare Turnstile
CloudFlare’s Turnstile is a free tool that replaces the CAPTCHAs used in reported attacks. This legitimate service allows website owners to easily add the necessary Turnstile code to their content, allowing users to simply click on a CAPTCHA instead of having to solve it.

From an attacker’s perspective, using this free tool is attractive because it requires the user to click on the CloudFlare Turnstile before being redirected to the phishing page. This adds a layer of protection for attackers because the final phishing payload is hidden from online URL scanners.
Man-in-the-middle attack phishing technique
Traditional phishing techniques often collect credentials before displaying an error page or redirecting the user to a legitimate login page. This approach tricks the user into thinking they entered incorrect credentials, most likely leaving them unaware of the fraud.
The man-in-the-middle phishing technique is more subtle. It collects the user’s credentials and immediately uses them to log into legitimate services. Also known as transparent phishing, this method allows users to successfully log in after the fraudulent credentials have been stolen, making the attack less noticeable.
Malicious QR codes are difficult to detect
“No one can read a QR code with their own eyes,” Damon Neville said. “You can only scan it with a suitable device, such as a smartphone. Some links are so long that you can’t check the entire link if you check it… but who would check a link?”
Since QR codes are images, text-only detection is not effective for them. There is also no widespread standard for verifying the authenticity of QR codes. Security mechanisms such as digital signatures for QR codes are uncommon, making it difficult to verify the origin or integrity of the content.
How to protect QR codes from phishing?
However, many QR code readers offer a URL preview, allowing users to see the URL before scanning. If there is any doubt about the URL, users should not use the QR code. In addition:
- QR codes that result in actions such as logging in or providing information should be viewed with suspicion and analyzed carefully.
- Security solutions may also be helpful as they can detect phishing URLs. URLs should always be scanned with such tools.
- Payment Unless you are sure it is legitimate, you should not proceed via QR code.
Microsoft Sway isn’t the only possibility Used Used by cybercriminals to host phishing pages.
“We regularly observe legitimate websites or applications being used to host phishing or vishing, such as Github, Gitbooks, or Google Docs, every day,” Damonneville said. “Not to mention all the URL shorteners or free hosting sites on the market, which are widely used to easily hide URLs.”
This again emphasizes that users consciousness Increased vigilance is required, and employees need to be trained to differentiate between suspicious and legitimate URLs.
Disclosure: I work at Trend Micro, but the opinions expressed in this article are my own.
[ad_2]
Source link


