
[ad_1]
New research from cybersecurity firm Volexity reveals A Chinese cyber espionage threat actor called StormBamboo deployed highly sophisticated attacks.
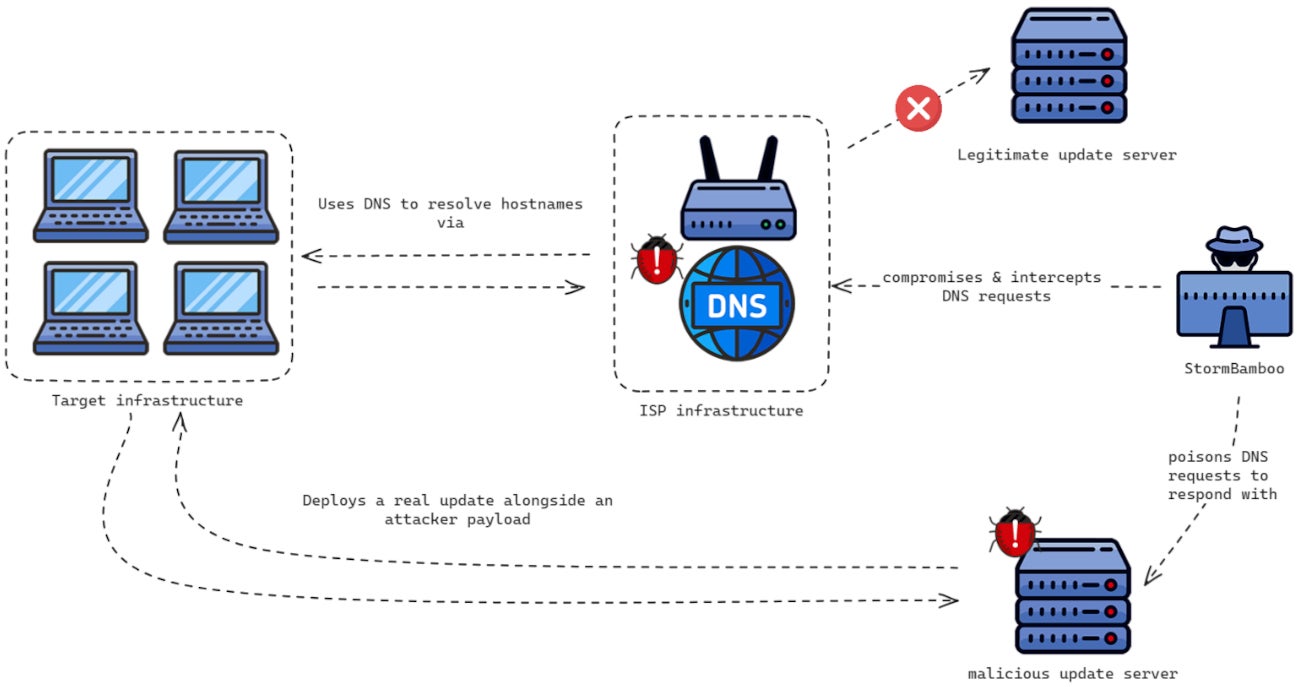
Threat actors compromised an ISP and modified the system’s DNS responses to queries requesting legitimate software updates. Multiple software vendors were targeted. In addition to legitimate update files, the modified responses caused StormBamboo to deliver malicious payloads. These payloads targeted macOS and Microsoft Windows operating systems.
Who is StormBamboo?
StormBamboo (aka Evasive Panda, Daggerfly, or Bronze Highland) is a China-aligned cyber espionage threat actor that has been active since 2012. The Chinese-speaking group has targeted numerous organizations aligned with China’s global interests.
Over the years, the group has targeted individuals in mainland China, Hong Kong, Macau, and Nigeria. In addition, the group has targeted entities such as governments in Southeast Asia, East Asia, the United States, India, and Australia.
The group has a long history of compromising legitimate infrastructure to infect its targets’ custom Malware Developed for Microsoft Windows and macOS operating systems. The team has deployed Watering Hole Attackwhich involves hacking into specific websites, targeting their visitors and infecting them with malware.
StormBamboo is also capable of launching supply chain attacks, such as compromising software platforms, to covertly infect people with malware.
The organization can also target Android user.
ISPs under attack, DNS responses poisoned
Threat actors seek to compromise a target’s ISP infrastructure to control the DNS responses from that ISP’s DNS servers—essentially translating domain names into IP addresses, thus directing them to the correct website. An attacker who controls the server can cause a computer to request a specific domain name from an IP address controlled by the attacker. This is exactly what StormBamboo did.
While it’s unclear how the group was able to compromise the ISP, Volexity reports that the ISP rebooted and took various components of its network offline, immediately halting the DNS poisoning operation.
The attacker’s goal was to alter the DNS answers for several different legitimate application update websites.
look: Why your company should consider implementing DNS Security Extensions
Paul Rascagneres, a threat researcher at Volexity and an author of the publication, said in a written interview with TechRepublic that the company doesn’t fully understand how threat actors choose ISPs.
“The attackers likely did some research or reconnaissance to determine what the victim’s ISP was,” he wrote. “We don’t know if other ISPs were also compromised; identifying it from the outside is complicated. StormBamboo is an aggressive threat actor. If this mode of operation is successful for them, they may use it on other ISPs to attack other targets.”
Legitimate update mechanism abused
Several software vendors were targeted in this attack.
Once a user’s DNS request is sent to the infected DNS server, it answers with an attacker-controlled IP address that delivers the real update for the software — but with the attacker’s payload.
According to a report by Volexity, several software vendors that use insecure update workflows have expressed concerns and released a new security update tool called 5K Player.
The software checks for updates to “YoutubeDL” every time it is launched. The check is done by requesting a configuration file that indicates if a new version is available. If so, it is downloaded from a specific URL and executed by the legitimate application.
However, the infected ISP’s DNS directed the application to a modified configuration file, indicating that there was an update, but one that delivered a backdoored YoutubeDL package.
The malicious payload is a PNG file that contains either the MACMA or POCOSTICK/MGBot malware, depending on which operating system the update is requested for. MACMA infects MacOS, while POCOSTICK/MGBot infects Microsoft Windows operating systems.
Malicious Payload
POCOSTICK, also known as MGBot, is a custom malware that was probably developed by StormBamboo, as it is reported that EssertThe malware has been around since 2012 and contains multiple modules that enable keylogging, file stealing, clipboard interception, audio stream capture, cookie and credential theft.
Instead, MACMA allows keylogging, fingerprinting of victim devices, and screen and audio capture. It also provides a command line to the attacker and has file stealing capabilities. Google initially reported the existence of the MACMA malware in 2021 and deployed it using a watering hole attack.
The Google attack was not initiated by a threat actor, but targeted visitors to the websites of a Hong Kong media outlet and a prominent pro-democracy labor and political group, according to Google. The attack was consistent with StormBamboo’s targeting.
Volexity also noticed significant code similarities between the latest version of MACMA and another malware family, GIMMICK. Storm Threat actors.
Finally, after the victim’s macOS device was compromised, Volexity discovered that the attacker deployed a malicious Google Chrome extension. The obfuscated code allowed the attacker to exfiltrate the browser’s cookies to a Google Drive account controlled by the attacker.
How can software vendors protect users from cyber threats?
Rascagneres told TechRepublic that Volexity found several targeted insecure update mechanisms from different software: 5k Player, Quick Heal, Sogou, Rainmeter, Partition Wizard, and Corel.
When asked how to protect and improve update mechanisms at the software vendor level, the researchers insisted that “software editors should enforce HTTPS update mechanisms and check the SSL certificates of websites from which updates are downloaded. In addition, they should sign updates and check this signature before executing them.”
To help companies detect StormBamboo activity on their systems, Volexity provides YARA rules to detect different payloads and suggest indicators of compromise that can block a company’s activity. supply.
Disclosure: I work at Trend Micro, but the opinions expressed in this article are my own.
[ad_2]
Source link


