
[ad_1]
Recent Research Cybersecurity firm ESET has provided details of a new attack campaign targeting Android smartphone users.
The cyberattack was based on a sophisticated social engineering scheme and the use of a new type of Android malware capable of stealing users’ Near Field Communication data to withdraw cash from NFC-enabled ATMs.
Threat actors continue to improve their techniques
ESET noted that the threat actors initially exploited Progressive Web Apps technology, which allows apps to be installed from any website other than the Play Store. The technology works with supported browsers, such as Chromium-based browsers on desktop or Firefox, Chrome, Edge, Opera, Safari, Orion, and Samsung Internet Browser.
PWAs are accessible directly through the browser, are very flexible, and usually do not present compatibility issues. Once a PWA is installed on the system, it can be identified by its icon, which displays an additional small browser icon.

Cybercriminals use PWAs to direct unsuspecting users to full-screen phishing sites to collect their credentials or credit card information.
The threat actors involved in this campaign have shifted from PWAs to WebAPK, a more advanced form of PWA. The difference between the two is subtle: PWAs are apps built using web technologies, while WebAPK uses a technology that integrates PWAs as native Android apps.
From an attacker’s perspective, using WebAPKs is stealthier because their icons no longer display a small browser icon.

The victim downloads and installs a standalone app from the phishing website. The person installs the app without requesting any additional permissions from the third-party website.
These fraudulent websites often imitate Some features of the Google Play Store can confuse users into thinking that the content they are installing is from the Play Store, when in fact it comes directly from a fraudulent website.
NGate malware
On March 6, the same distribution domains used for observed PWA and WebAPK phishing campaigns suddenly began to spread a new malware called NGate. Once installed and executed on the victim’s phone, it opens a fake website that asks the user to enter banking information, which is then sent to the threat actor.
However, the malware also embeds a NFCGatewhich is a legitimate tool that allows passing NFC data between two devices without the need for the devices to be rooted.
Once the user provides banking information, the person receives a request to activate the NFC feature from their smartphone and holds the credit card against the back of the smartphone until the app successfully recognizes the card.
Complete social engineering
While activating NFC for the app and recognizing the payment card may initially seem suspicious, the social engineering techniques deployed by the threat actors explain this situation.
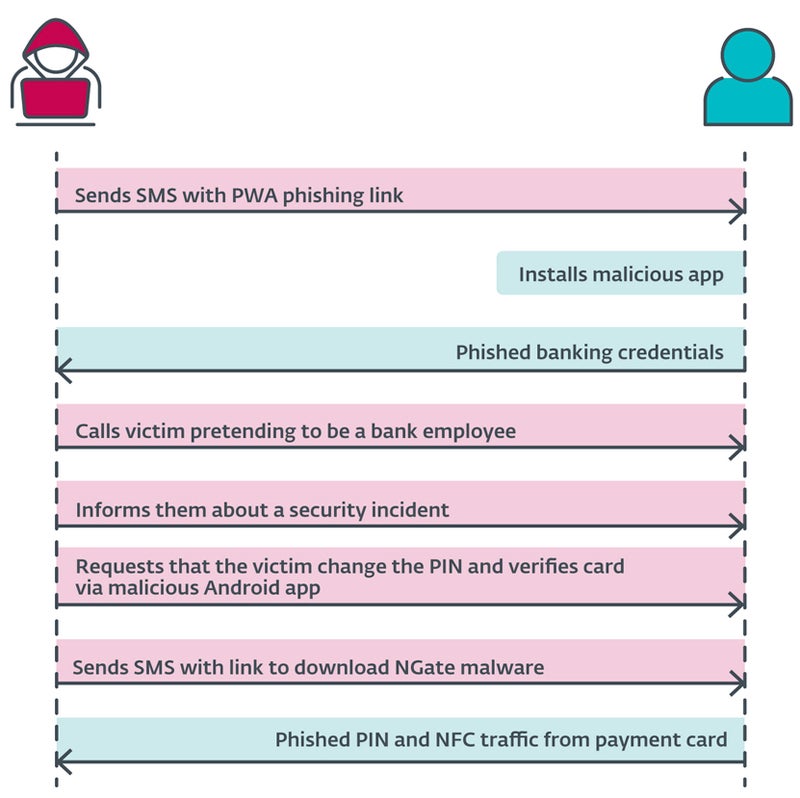
Cybercriminals send users a text message that mentions tax returns and contains a link to a phishing website that impersonates a banking company and directs users to the malicious PWA. Once installed and executed, the app asks users for banking credentials.
At this point, the threat actor will call the user, impersonating the bank company. The victim will be informed that their account has been compromised, most likely due to the previous text message. The user will then be prompted to change their PIN and verify their bank card details using a mobile app to protect their bank account.
The user then receives a new text message containing a link to the NGate malware app.
Once installed, the app requests activation of the NFC feature and identifies the credit card by pressing it against the back of the smartphone. The data is sent to the attacker in real time.
Monetization of stolen information
The information stolen by attackers can be used for common frauds: withdrawing money from a bank account or using credit card information to buy goods online.
However, the NFC data stolen by cyber attackers allowed them to impersonate original credit cards and withdraw money from ATMs using NFC, a previously unreported attack vector.
Attack Range
ESET’s research shows that the attack took place in the Czech Republic, as only banking companies were targeted in the country.
A 22-year-old suspect was arrested in Prague. He was in possession of about 6,000 euros ($6,500). According to Czech police, this money was stolen from the last three victims, suggesting that the threat actor stole more money in this attack campaign.
However, as the ESET researchers wrote, “the possibility of its expansion to other regions or countries cannot be ruled out.”
In the near future, more cybercriminals are likely to use similar techniques to steal funds via NFC, especially as NFC becomes more popular. Popular For developers.
How to protect against this threat
To avoid falling victim to this cyber campaign, users should:
- Verify the source of downloaded applications and double-check the URL to ensure its legitimacy.
- Avoid downloading software from sources other than official sources, such as the Google Play Store.
- Avoid sharing their payment card PIN. No bank will ask for this information.
- Use digital versions of traditional physical cards, as these virtual cards are securely stored on your device and can be protected with additional security measures like biometric authentication.
- Install security software on your mobile device to detect malware and unwanted apps on your phone.
Users should also deactivate NFC when their smartphones are not in use to protect them from additional data theft. Attackers can read card data through wallets, purses and backpacks left unattended in public places. They can use this data to make small contactless payments. Protective cases can also be used to effectively block unwanted scans.
If you have any questions when a bank employee calls you, hang up and call your usual bank contact, preferably from another phone.
Disclosure: I work at Trend Micro, but the opinions expressed in this article are my own.
[ad_2]
Source link

