
[ad_1]
In August, a hacker leaked 2.7 billion data records, including social security numbers, to a dark web forum in one of the largest data breaches in history. The owner of the data, National Public Data, has now acknowledged the incident and blamed a “third-party malicious actor” for the December 2023 breach.
The background check service agency statement It was published on August 12. It explains how to apply “additional security measures” to protect yourself from future incidents; however, it advises those affected to “take precautions” rather than offering any remedies.
Troy Hunt, security expert and creator of the Have I Been Pwned vulnerability checking service, investigated the leaked dataset and found that it only contained 134 million unique email addresses and 70 million rows in the US criminal records database. Email addresses have nothing to do with SSNs.
Other records in the dataset include a person’s name, mailing address and Social Security number (SSN), but some also contain other sensitive information, such as the names of relatives. Bloomberg.
How the data was stolen
The intrusion is related to an incident on April 8, when a well-known cybercrime group called USDoD Claims to have access to personal data of 2.9 billion people The information, which came from the United States, Britain and Canada, was sold for $3.5 million, according to a person familiar with the matter. Class Action ComplaintsThe U.S. Department of Defense is believed to have obtained the database from another threat actor using the alias “SXUL.”
The data was allegedly stolen from National Public Data (aka Jerico Pictures), which the criminals claimed contained records on every person in the three countries. At the time, malware site VX-Underground said the data dump did not include information on users who had used their data to opt out of the service.
“Not everyone who uses some kind of data to opt out of a service is present,” Posted in X.
look: The largest password leak in history: nearly 10 billion passwords leaked
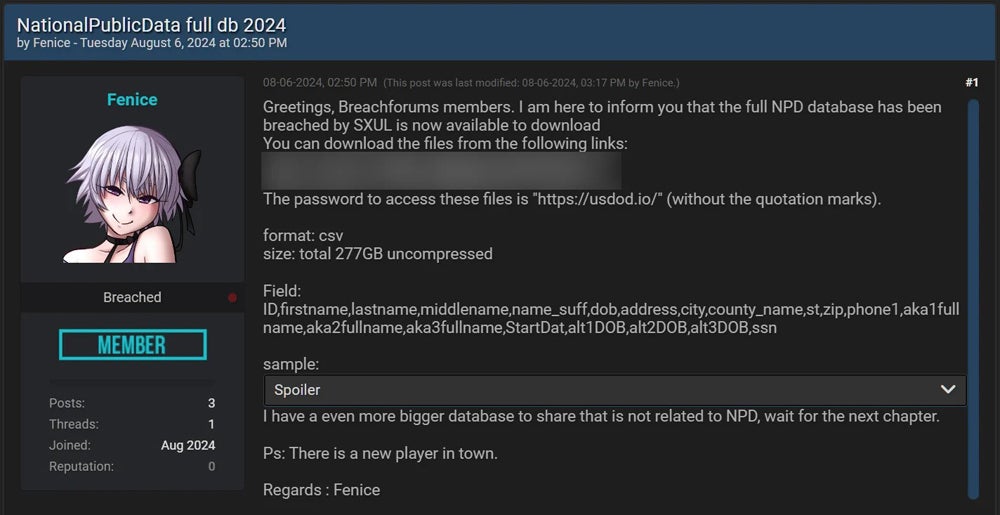
Subsequently, some cybercriminals released different samples of this data, which usually contained different entries and included phone numbers and email addresses. But it was not until the beginning of this month that a user named “Fenice” leaked 2.7 billion unencrypted records on the dark web called “Breached”. These records exist in the form of two csv files, totaling 277 GB. These files do not contain phone numbers and email addresses. Fenice said that the data came from SXUL.
National Public Data’s sister asset may offer an entry point
According to research Krebs on safetyhackers may have gained initial access to the state’s public data records through its sister company RecordsCheck, another background check service.
As of August 19, “recordscheck.net” hosted an archive called “members.zip” that contained source code and plain-text usernames and passwords for different components of its site, including its administrators. The archive showed that all users of the site used the same six-character password by default, but many never changed it.
Additionally, Krebs wrote that recordscheck.net was “visually similar to nationalpublicdata.com and had the same login page.” National Public Data founder Salvatore “Sal” Verini later told Krebs that “members.zip” was “an old version of the site and the code and passwords didn’t work” and that RecordsCheck would cease operations “in the next week or so.”
In addition to the plaintext passwords, there is other evidence that RecordsCheck may have provided an entry point into Verini’s property. According to Krebs, RecordsCheck runs background checks on people by querying records from national public data databases and a data broker called USInfoSearch.com. Many USInfoSearch accounts hacked and are exploited by cyber criminals.
Not all of the 2.7 billion records leaked are accurate or unique, but some are
Since each person has multiple records associated with them, one for each previous home address, this leak would not expose the information of 2.7 billion people. Beep Computersome of the affected individuals have confirmed that the SSN associated with their information in the data dump was incorrect.
BleepingComputer also found that some records did not contain the current addresses of the individuals involved, suggesting that at least some of the information was outdated. However, others confirmed that the data contained legal information for them and their families, including those who had died.
The class action complaint also alleges that NPD scraped billions of individuals’ personally identifiable information from non-public sources to create their profiles. This means that those affected may not have intentionally provided their data. People living in the United States are particularly likely to have been affected by this breach in some way.
Several websites have been set up to help individuals check if their information has been exposed in national public data breaches, including npdpentester.com and npdbreach.com.
Experts interviewed by TechRepublic recommend that individuals affected by the breach consider monitoring or freezing their credit reports and remain vigilant against phishing campaigns targeting their emails or phone numbers.
Businesses should ensure that all personal data they hold is encrypted and stored securely. They should also implement other security measures such as multi-factor authentication, password managers, security audits, employee training and threat detection tools.
look: How to avoid data breaches
TechRepublic has reached out to Florida-based National Public Data for a response. The company is currently accepting Schubert Jonker & Kolbe Law Office.
Plaintiff Christopher Hofmann said that on July 24, he received a notification from his identity theft protection service provider informing him that his personal information had been compromised through the “nationalpublicdata.com” breach and posted on the dark web.
What security experts think of the breach
Why are national public data records so valuable to cybercriminals?
Jon Miller, CEO and co-founder of anti-ransomware platform Halcyon, said that from a criminal’s perspective, the value of national public data records comes from the fact that they are collected and organized.
“While much of this information is already in the hands of attackers, they would have to spend a lot of effort and money to collect similar data, so NPD is simply doing them a favor and making it easier,” he told TechRepublic in an email.
look: How organizations should handle data breaches
Oren Koren, chief product officer and co-founder of security platform Veriti, added that information about deceased people could be repurposed for nefarious purposes. “With this ‘starting point,’ individuals can attempt to create birth certificates, voting certificates, etc., which are valid because they have some of the information they need, most importantly a social security number,” he told TechRepublic in an email.
How to stop data aggregator breaches?
“Background check companies like National Public Data are essentially data brokers that collect as much identifying information as possible about everyone and then sell it to anyone willing to pay,” Paul Bischoff, consumer privacy advocate at tech research firm Comparitech, told TechRepublic in an email. “They collect vast amounts of data without the knowledge or consent of the data subjects, most of whom have no idea what National Public Data is or does.”
“We need stricter regulation of data brokers, more transparency, requiring them to notify data subjects when their information is added to a database, restricting web scraping, and allowing data subjects to view, modify, and delete data.
“National Public Data and other data brokers should be required to tell data subjects where their information originally came from so that people can take proactive steps to protect their privacy at the source. In addition, there is no reason not to encrypt compromised data.”
Miller added: “The monetization of our personal information, including personal information we choose to make public, goes well beyond the protections of laws that govern who can collect what information, how it is used, and, most importantly, what their responsibilities are in protecting it.”
Can businesses and individuals prevent themselves from becoming victims of data breaches?
Chris Deibler, vice president of security at security solutions provider DataGrail, said many of the cyber hygiene principles for businesses and individuals won’t be very helpful in this situation.
“In this environment, reasonable measures for individuals to protect themselves have reached their limits, and real solutions will need to be implemented at the corporate and regulatory levels, including normalizing data privacy regulation through international treaties,” he told TechRepublic in an email.
“Right now, the balance of power is not in favor of individuals. GDPR and the introduction of state and national regulations are good moves, but the prevention and consequence model currently in place is clearly not going to prevent large-scale data aggregation.”
[ad_2]
Source link


